What is a VPN? Meaning and what it’s used for
A VPN (virtual private network) is a tool that creates an encrypted tunnel for your data, protects your online identity by hiding your IP address, and allows you to use secure servers on all networks. With MeteorVPN, you can protect your internet connection and increase your privacy online.
VPN definition
VPN stands for “virtual private network”:
- It’s “virtual” because of the way MeteorVPN creates a simulated, encrypted connection over the internet instead of using a dedicated, physical connection.
- It’s “private” because MeteorVPN’s encryption process shields your traffic from prying eyes.
- It’s a “network” because MeteorVPN securely connects your device to a remote network.

What does a VPN do?
What is a VPN used for?
Why choose VPN?
How does a VPN work?
VPN components
Why use a VPN?
VPN disadvantages
Types of VPN
VPN protocols
What does a VPN do?
A VPN reroutes your traffic through a remote MeteorVPN server, encrypting it in the process, and protects it from snoopers. It also changes your IP and virtual location — your real one remains private, and you get a new IP that belongs to the MeteorVPN server you’re connected to. This ensures extra security and significantly increases your privacy online — no one knows what city or country you’re browsing from.
If you want to keep your browsing private, reduce your digital footprint, and increase your online security, then MeteorVPN is a perfect tool to do it. But a VPN might not be needed if you don’t have any privacy concerns, only use trusted secure websites, and don’t care about third-party tracking.
What is a VPN used for?
You should use MeteorVPN whether you’re browsing, streaming, gaming, or shopping. Why? Because these days, your every click online is being recorded — and no one likes to be watched or tracked, even if they have nothing to hide.
Connecting to public Wi-Fi
MeteorVPN lets you browse with more security and privacy on public Wi-Fi by encrypting your connection. Hackers have many methods to steal your data on public hotspots, but when you use MeteorVPN, your online traffic is invisible to them.
Traveling
MeteorVPN lets you securely access your paid home content while traveling around the world. Install the MeteorVPN app on your phone, tablet, or laptop, and never miss a social media trend or your favorite show’s season finale.
Why choose VPN?
If you’re looking for the best VPN out there, give MeteorVPN a chance. It’s fast, reliable, and offers flexible plans suited to your needs.
How does a VPN work?
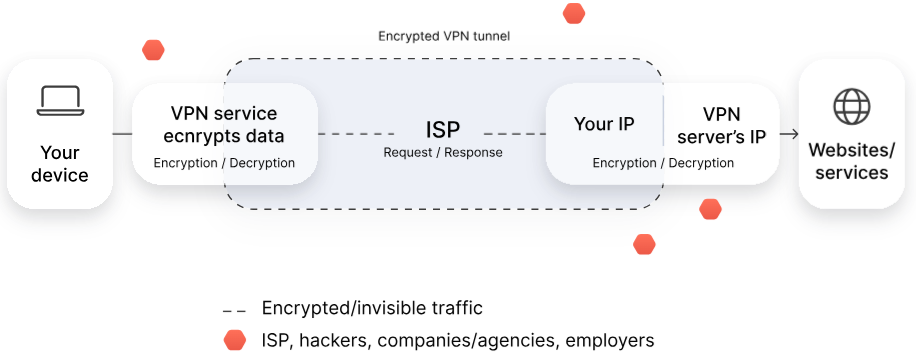
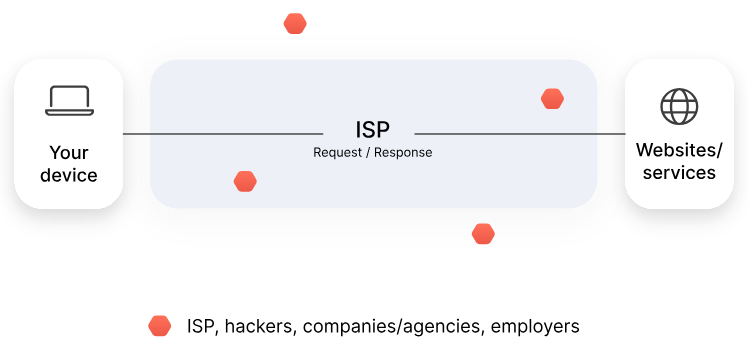
MeteorVPN works by creating a secure encrypted connection between your device and a remote server. This way, your data can travel in secrecy instead of through your internet service provider. MeteorVPN changes your real IP address and encrypts your internet connection to make your browsing safer and more private.
With VPN
Without VPN
What are the components of a VPN?
VPN client
What is a VPN client in the context of creating a private network?
A MeteorVPN client is software that allows your device to connect to a MeteorVPN server, creating a safer, encrypted connection to a private network over the internet. It acts as the gateway for your device to communicate securely with the MeteorVPN server.
VPN Server
What is a VPN server, and how does it provide a secure endpoint?
A MeteorVPN server is a remote server that’s configured to receive and send encrypted data to MeteorVPN clients that are connected to it. This process changes your IP address and virtual location as well, giving you more privacy and security.
VPN Protocol
What is a VPN protocol, and how does it encrypt your traffic?
A VPN protocol is a set of rules that determines how data travels between your device and a MeteorVPN server. It decides how the connection is established, how encryption is applied, and how data is transferred.
VPN Tunnel
What is a VPN tunnel, and how does it ensure privacy?
A VPN tunnel is a secure, encrypted connection that allows your data to travel safely between your device and the MeteorVPN server. Strong encryption algorithms make this tunnel private, preventing third parties from intercepting or monitoring your online activity.
VPN Tunnel
What is a VPN connection, and how does it define the overall process?
A MeteorVPN connection is the result of the collaboration between the MeteorVPN client, server, protocol, and tunnel. The client connects to the server using a secure protocol, creating an encrypted tunnel that securely transmits your data, ensuring increased privacy and protection throughout the entire process.
Why use a VPN?
MeteorVPN is a virtual private network (VPN) service that encrypts your internet connection and hides your IP address, ensuring your online activities remain private and secure. By routing your traffic through secure servers around the world, MeteorVPN helps protect your data from hackers, ISPs, and trackers.
Privacy online
Changing your IP address, hiding your virtual location, and encrypting your connection allow you to increase your privacy online.
Digital Security
A VPN shields you from cyber threats, like man-in-the-middle attacks, packet sniffing, and dangerous Wi-Fi networks.
Open Internet
With a VPN, you can avoid censorship and restrictions and enjoy the free and open internet.
Safe Data Sharing
Share files securely while at home or at work — a VPN encrypts your connection so that no snoopers can see what data you’re transferring.
VPN Disadvantages
Using a VPN will give you more peace of mind, but it does come with a few caveats:
Reduced Speeds
The encryption process and the extra distance your data travels to and from the VPN server will slow down your connection at least a little bit.
Compatibility Issues
Some websites or services may block or restrict access from known VPN servers.
Cost
Reliable and secure VPN services will require a subscription.
CAPTCHAs
Using a VPN can make your encounter more CAPTCHA prompts.
Types of VPN?
There are many VPN types, but the vast majority of them fall into five main categories:
Personal VPN
Most consumer-grade VPNs are classed as personal VPNs, including NordVPN. They are very similar to remote-access VPNs in operation, but instead of connecting to a proprietary restricted network (such as your workplace), you connect to your VPN provider’s servers for protection and privacy while you explore the internet. Personal VPNs are best for individual users’ needs.

Site-to-site VPN
Site-to-site VPNs are mostly used by businesses — large corporations in particular. They allow users in selected locations to access each other’s networks securely. It’s a great way to connect all offices and enable different branches to safely share resources and information. A site-to-site VPN is an essential collaboration tool for businesses with multiple offices.
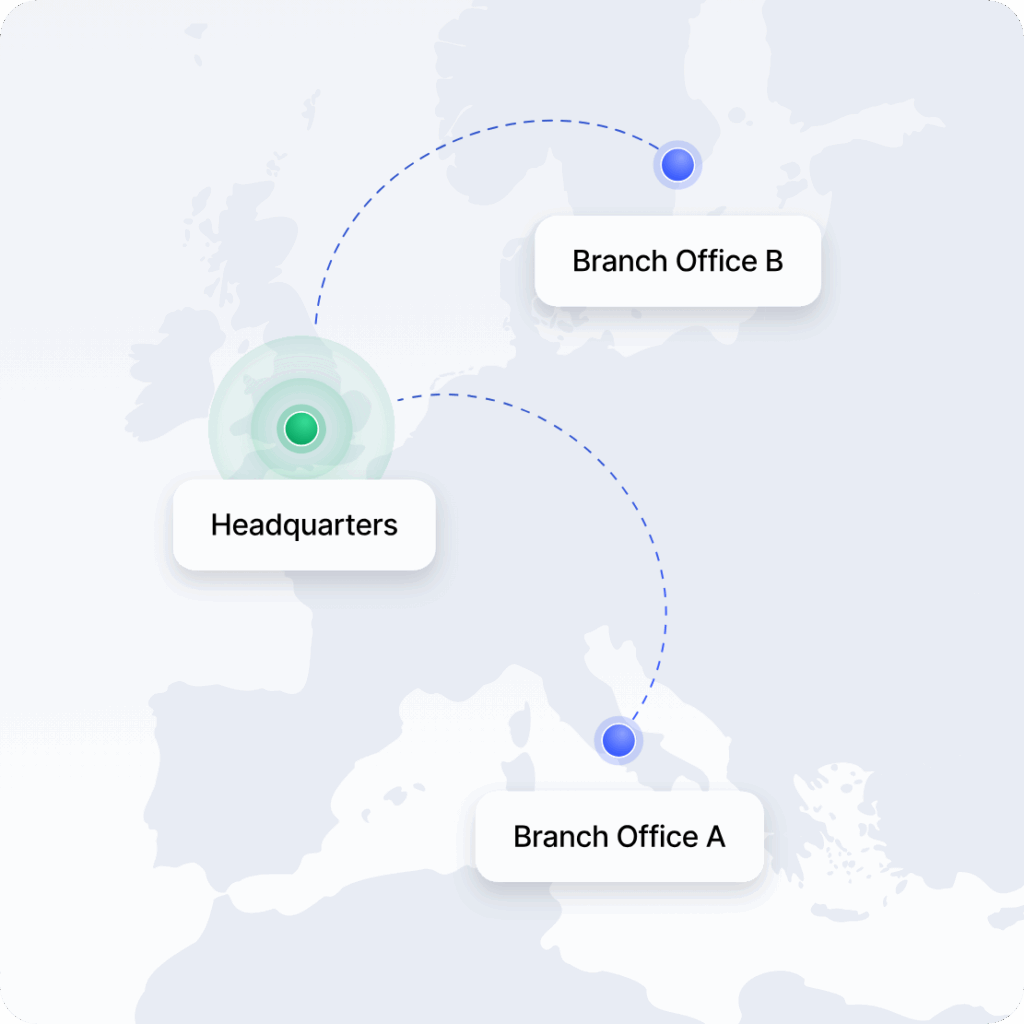
Remote access VPN
A remote-access VPN allows users to connect to a remote network, usually by using special software. If you ever needed to log on to your office network, you most likely used a remote access VPN as well. It makes working away from the office safer and easier, as employees can access data and resources from anywhere. Remote access VPNs are perfect for remote workers.

Mobile VPN
A mobile VPN is designed to provide reliable VPN connections for mobile devices. These VPNs are optimized to maintain a stable connection even as the user moves between different networks, like switching from Wi-Fi to mobile data. Mobile VPNs are ideal for people who need to stay connected and protected on the go.
Browser VPN proxy extension
A VPN proxy extension is a lightweight option for securing your browsing. You can install it on your browser and reroute your web traffic through a VPN, leaving other apps on your device unaffected. It doesn’t offer full device-wide protection like traditional VPN apps, but it’s perfect for people who need a quick way to change their IP without overloading their device.
VPN Protocols
Different types of VPN protocols have different advantages, so most VPN providers offer at least two. NordVPN allows you to choose between OpenVPN, NordWhisper, and NordLynx protocols in its apps, and you can also opt for IKEv2/IPSec protocol for manual configurations.
OpenVPN
OpenVPN is the most popular encryption protocol, currently used by the majority of VPN providers in the world. One of OpenVPN’s biggest strengths is that it is highly configurable. It also offers a nice balance between speed and security because you can use it on both TCP and UDP ports. While the TCP port is a more stable option, UDP is faster, and many users prefer it for a seamless online gaming and live streaming experience.
IKEv2/IPSec
IKEv2/IPSec is a IKEv2 tunneling protocol, which is paired with IPSec for encryption. It has the ability to restore a secure connection after the internet drops and adapts well to changing networks. This functionality could be useful to smartphone users who often switch between home Wi-Fi and mobile connections or move between hotspots.
WireGuard®
WireGuard® is a relatively new, high-performance VPN protocol, widely considered to be the fastest VPN protocol out there. What makes WireGuard so fast? The secret lies in its code — all 4000 lines of it. Compare that to the tens of thousands of lines in other VPN protocols, and you’ll see why it’s so mind-blowingly quick.
NordLynx
If you’re looking for both privacy and speed, NordLynx is the way to go. It’s our default protocol, a unique tech solution based on WireGuard®. NordLynx allows users to enjoy a fast internet connection without compromising their security.
L2TP/IPSec
Layer 2 Tunneling Protocol (L2TP) is a method for transmitting data from one device to another. As L2TP doesn’t offer any kind of encryption, it almost always comes together with Internet Protocol Security (IPSec), which negotiates the cryptographic keys to create a VPN-like environment. It’s a highly secure protocol but can be very slow because it encapsulates data twice.
PPTP
PPTP is the most commonly used protocol that supports thousands of operating systems and devices. It’s also easy to set up, without the need to install additional software. However, PPTP is decades-old and not as secure as other protocols available today.
SSTP
Secure Socket Tunneling Protocol is a suitable alternative to standard protocols in areas where VPNs are restricted because it can bypass most firewalls. SSTP is similar to OpenVPN but it is owned by Microsoft, which means it is not available for independent auditing.
NordWhisper
Whisper is the newest addition to the VPN protocol family. It’s designed specifically to allow users to connect to VPN servers from networks that usually limit traditional VPN traffic. By using NordWhisper, users can get a smoother and more consistent browsing experience, even in restrictive environments.
Which VPN protocol is the best?
There isn’t a one-size-fits-all answer — different protocols are suited to different use cases. For example, if you need the fastest speeds for streaming or gaming, you should choose a protocol based on WireGuard®, like NordLynx. For mobile users who need stable connections when switching between networks, IKEv2/IPSec is a strong choice. And NordWhisper is your best bet if you need to bypass restrictions in highly controlled networks.
FAQ
What is MeteorVPN and how does it work?
MeteorVPN is a virtual private network (VPN) service that encrypts your internet connection and hides your IP address, ensuring your online activities remain private and secure. By routing your traffic through secure servers around the world, MeteorVPN helps protect your data from hackers, ISPs, and trackers.
Does MeteorVPN keep any logs of my online activity?
No, MeteorVPN follows a strict no-logs policy. This means it does not track, store, or share any information about your browsing history, connection timestamps, or data usage. Your privacy and anonymity are always protected.
Why is MeteorVPN one of the best VPN providers?
Meteor VPN protects your online privacy by hiding your real IP address. With your virtual location hidden, it’s much harder for your online activity to be monitored, restricted, or sold to advertisers.
